[ad_1]
Australian identity access management professionals have been urged to entrench identity as a foundation of their organisations’ cyber security posture, as sub-par management of significant exposures, including machine identities, was putting many organisations at risk.
Gartner VP analyst Felix Gaehtgens, speaking at Gartner’s Security & Risk Management Summit in Sydney, argued IAM practitioners should champion investment in mature IAM programs, centred around an identity fabric approach within their organisations.
Organisations could enhance resilience through better IAM hygiene, Gaehtgens said. He warned against allowing tech vendors to lock data into silos and use AI without getting the data right first. One suggestion was to take a product management approach to engaging different stakeholders.
IAM now at the core of a mature cyber security posture
IAM leaders have faced a fundamental shift in the identity landscape over the last few years, Gaehtgens said. This was primarily due to the reality they were now “expected to create centralised control in a totally decentralised world” in order to protect cyber security.
Employees working from anywhere had eroded the value of legacy security controls at the perimeter, Gaehtgens said, while assets, data and applications were now being protected with different types of access controls — many implemented by third parties like cloud vendors.
PREMIUM: Consider creating a cloud security policy.
“The CISO is asked three main questions by the board: ‘Are we secure?’, ‘Are we compliant?’ and ‘What about AI?’” Gaehtgens said. “IAM is at the centre of all this. The role is becoming much more important. Why? Because it is at the centre of security in the new world.”
The rise of machine identities
The growth of machine identities, in addition to human identities, had become a “big problem,” Gaehtgens said. There are now between 10 and 45 times as many machine identities in an organisation, many of them heavily privileged, making them a huge, unmanaged cyber risk.
Organisations should put identity first with mature IAM program
Moving identity to the centre of cyber security is key, Gaehtgens said.
“Many of you have a lot of tools but don’t really have a good, functioning IAM program — here is your opportunity,” said Gaehtgens. “It is the control plane and foundation of cyber security — this is where focus need to be.”
IAM programs should make identity management “consistent, contextual and continuous” and be enabled by IAM leaders willing to build relationships outside of IT.
Consistent
According to Gaehtgens, global regulations are designed to protect personal data wherever it may be, including in databases, unstructured files, in motion or at rest. Gaehtgens said this means that, while organisations have a slew of tools, they need consistency in the access policies applied.
Contextual
Policies need to be dynamic and context-aware.
“Just because someone can access a folder doesn’t mean they should be downloading 30 documents a minute — that’s not typical for a human being, and might indicate their account has been taken over by a bot,” Gaehtgens said.
Continuous
The future will see continuous adaptive trust applied throughout sessions. Gaehtgens said single sign-off was coming, which would involve the ability to terminate multiple sessions across systems based on user events, something he said would become normal for users.
Leadership
To put in place an IAM program, IAM leaders will need to strengthen relationships beyond IT. Gaehtgens urged IAM leaders to learn the language of business, including finance and legal, so they can measure and communicate about IAM in terms like business value and risk.
SEE: A top IAM solution can help strengthen cyber security efforts.
Success could be easier with a product management approach. Gaehtgens said there is a trend towards product management approaches to IAM programs, which is leading to an acceleration in business value and delivery through a “highly cross-functional” style.
Focus on identity fabric rather than IAM tools
A more cohesive, architecturally sound way of managing IAM is needed for the future, Gaehtgens said.
“Most organisations struggle with the delivery of basic IAM capabilities for humans and machines, even after years of investment in and work on this,” said Gaehtgens.
Embracing an identity fabric architectural approach
An “identity fabric” approach could help IAM pros tap into their current opportunities and free themselves from the shackles of vendor lock-in, Gaehtgens said. He put forward a framework of 10 principles Gartner uses to guide clients towards an identity fabric model (Figure A).
These include expanding the scope to include:
- Machine identities, responsible for many “credential leakage takeovers.”
- Event-based connectivity, rather than static batch analysis
- Composable “and, in the long run, compostable” architecture that can flex through change.
Working with topology could enable organisations to gain centralised control in a decentralised environment by ripping functions out of tools with an abstraction layer. This sees the functions of underlying tools connected at a higher level to orchestrate them for different use cases.
AI capabilities could boost IAM team productivity
AI is likely to take on aspects of IAM, such as account takeover detection and user entity behaviour analytics. It could also recommend right-sized access policies from entitlement data or help integrate applications with IAM services, including coding and configuration updates.
Gaehtgens cautioned that the data needed to be right, and data management and engineering could become a formal capability for an IAM program.
“AI can deliver some value as long as you also work on the necessary data management and data engineering dependencies,” Gaehtgens said.
Identity hygiene the first line of cyber security defence
IAM is “the first line of defence in reducing the number of alerts going through to your (security operations centre),” Gaehtgens said. This means IAM professionals need to focus on identity hygiene to boost prevention and detection, including with machine identities.
SEE: Explore the difference between IAM and PAM solutions
IAM teams can start with lower effort activities such as account existence (Figure B). However, Gaehtgens said while Australia’s Essential Eight framework recommends tackling machine identities at Maturity Level 3, it should be something organisations look at before then.
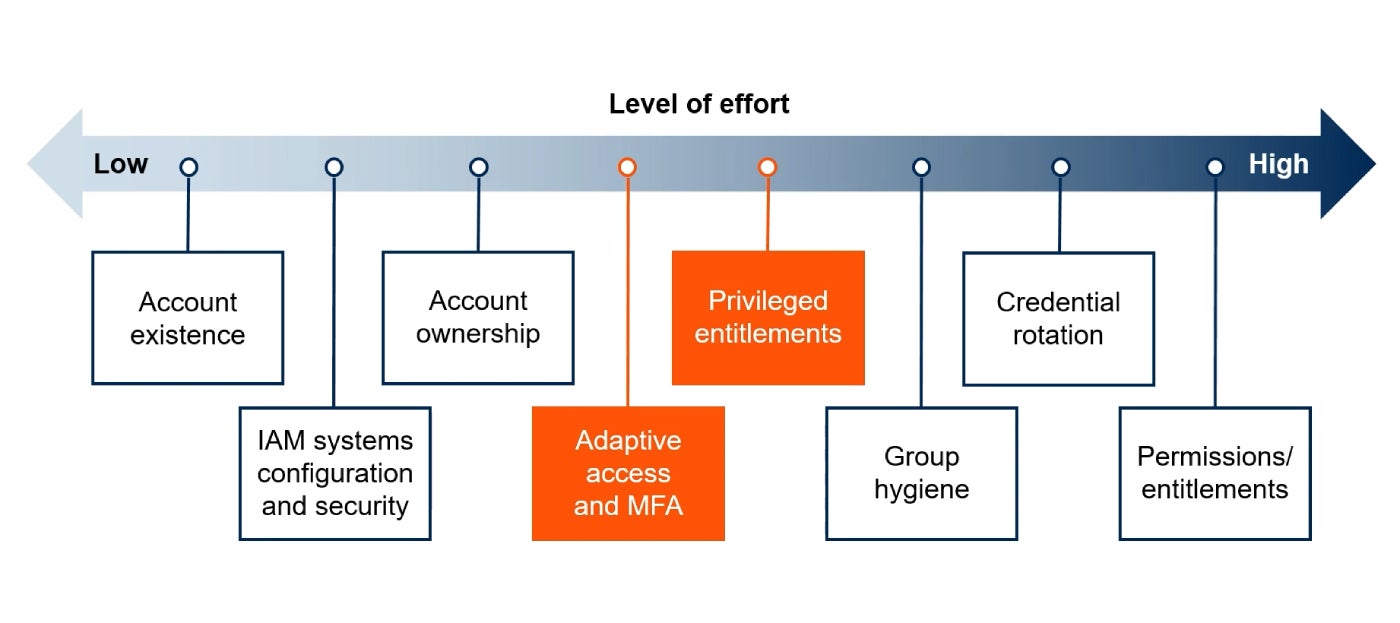
He recommended IAM configuration vigilance.
“I’ve seen live IAM systems configured with privileged access for testing something that was never removed,” Gaehtgens said. “If anyone got wind of that, they could take over that IAM system and could change the roles to whatever they wanted.”
IAM teams could also pursue activities with mid-level of effort, like rolling out adaptive access and MFA.
“The key is balance between investment in hygiene and threat detection and response,” Gaehtgens said. “The better we are at prevention, the less comes through for detection.”
[ad_2]
Source link

